Intel AMT, allows enhanced hardware-based isolation and recovery for embedded systems that go offline, and the Intel® Rapid Recover Technology, which allows embedded devices to recover data and return the system to an operational status in the event of hard drive failure or massive data corruption.
April 17, 2009
Intel VT-d Bios Support
A technology in the Intel Q35 chipset; Intel VT-d, provides advanced remote management capabilities for I/O devices. The technology enables partitioning of I/O devices to virtual machines to distribute system resources and protect assets. Intel VT-d will improve performance by increasing the bandwidth and lowering the latency attributed to software virtualization. Industrial automation applications and network appliances are two key segments that could benefit from this technology.
April 9, 2009
Extreme Summit 48s NAT Howto
This is a simple HOWTO configuration for NAT on an Extreme Summit 48s
This assumes two VLANs an internal and external:
Nat Configuration
The steps to get NAT running are:
- Add a NAT rule
- Set the NAT timeout
- Configure “internal” vlan(s)
- Configure “external” vlan(s)
- enable nat
Assuming you have an external vlan called “ext” and an internal block of IPs at 172.16.166.0/24 and an external address 198.168.0.10/32; you can use the following:
Configure a NAT rule
configure nat add “ext” map source 172.16.166.1/32 to 198.168.0.10/32
Configure the NAT timeout
configure nat timeout 300
Configure the internal VLAN for NAT
configure nat “webserver-internal” inside
Configure the external VLAN for NAT
configure nat ext outside
configure nat Default outside
Enable NAT
enable nat
That should be all there is to it. I hope this worked for you.
March 17, 2009
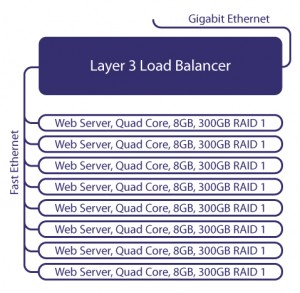
Extreme Summit 48i Server Load Balancing HOWTO
Concept and Network layout
Background
I have a client, who has a client, who has a client blah blah blah…
Unnamed Client – “We need a powerful webserver farm, and have a 10k budget for this project. We’ve already got a rack, and plenty of bandwidth. What do you recommend?”
Network Layout
Devices – Switch / Load Balancer
Among the list of their assets was a Summit 48i to work with. So, I have to work this device into the equation. Finding out that it had a Full layer 3 license was nice, because it would allow us to do Server Load Balancing.
The plan, setup a network with several web servers. The WANSecurity application servers do a great job for this. They’re fast, reliable and inexpensive. We’ll use the WANS-APP-1K for this which is a Quad Core processor with 8 GB of ram, 320GB RAID 1, and two on-board GigE interfaces.
Devices – Web Server
Switch Configuration
base configuration
In this case it was a good idea to completely erase all previous configuration from the switch. So that’s what I did.
unconfigure switch all
We have to setup a default base configuration on the switch. First we’ll create a VLAN, assign it an IP address and enable IP routing for it, and the default VLAN, and finally set a default gateway for outbound traffic.
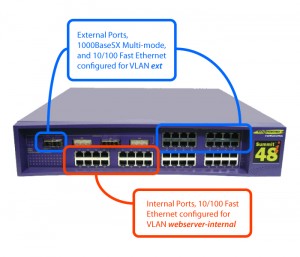
create vlan “ext”
configure vlan “ext” ipaddress 198.117.0.10 255.255.255.128
configure vlan “ext” add port 1 untagged
enable ipforwarding vlan “Default”
enable ipforwarding vlan “ext”
configure iproute add default 198.117.0.1 1
server load balancing configuration
First we’ll create a VLAN (webserver-internal) for all of the web servers to be connected to, and we’ll assign the VLAN an IP address.
create vlan “webserver-internal”
configure vlan “webserver-internal” ipaddress 172.16.166.254 255.255.255.0
Summit48si:21 #
* Summit48si:21 # create vlan “webserver-internal”
* Summit48si:22 # configure vlan “webserver-internal” ipaddress 172.16.166.254 255.255.255.0
IP interface for VLAN webserver-internal has been created.
IP address = 172.16.166.254, Netmask = 255.255.255.0.
* Summit48si:23 #
Next, we’ll assign interface ports to the VLAN (webserver-internal)
configure vlan webserver-internal add port 17
configure vlan webserver-internal add port 18
configure vlan webserver-internal add port 19
configure vlan webserver-internal add port 20
configure vlan webserver-internal add port 21
configure vlan webserver-internal add port 22
configure vlan webserver-internal add port 23
configure vlan webserver-internal add port 24
configure vlan webserver-internal add port 25
configure vlan webserver-internal add port 26
configure vlan webserver-internal add port 27
configure vlan webserver-internal add port 28
configure vlan webserver-internal add port 29
configure vlan webserver-internal add port 30
configure vlan webserver-internal add port 31
configure vlan webserver-internal add port 32
Now, we’ll enable server load balancing with the command enable slb, and tell the switch what type of server load balancing will be on each VLAN. Clients connect to “ext” and “Default”. Servers connect to “webserver-internal” VLAN.
enable ipforwarding
enable slb
configure vlan webserver-internal slb-type server
configure vlan ext slb-type client
configure vlan Default slb-type client
create slb pool web-pool lb-method least-connections
configure slb webservers add 172.16.166.1 : http
configure slb webservers add 172.16.166.2 : http
configure slb webservers add 172.16.166.3 : http
configure slb webservers add 172.16.166.4 : http
configure slb webservers add 172.16.166.5 : http
configure slb webservers add 172.16.166.6 : http
configure slb webservers add 172.16.166.7 : http
configure slb webservers add 172.16.166.8 : http
configure slb webservers add 172.16.166.9 : http
configure slb webservers add 172.16.166.10 : http
create slb vip webserver pool webservers mode translation 198.117.0.10 : http
Client Configuration
Linux (Ubuntu) Network Configuration
Finally, we configure our webservers for the webservers-internal VLAN.
cat /etc/network/interfaces
# This file describes the network interfaces available on your system
# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet static
address 172.16.166.1
netmask 255.255.255.0
network 172.16.166.0
broadcast 172.16.166.255
gateway 172.16.166.254
All set, customer is ready to configure their web servers as they see fit.
Enjoy!